Explore traditional Chinese festivals beyond New Year, including the Lantern Festival, Qingming, and more, uncovering rich customs and foods.


Explore traditional Chinese festivals beyond New Year, including the Lantern Festival, Qingming, and more, uncovering rich customs and foods.

Explore how PgDog transforms PostgreSQL scaling with no app code changes. Learn about its features, deployment, and best practices.
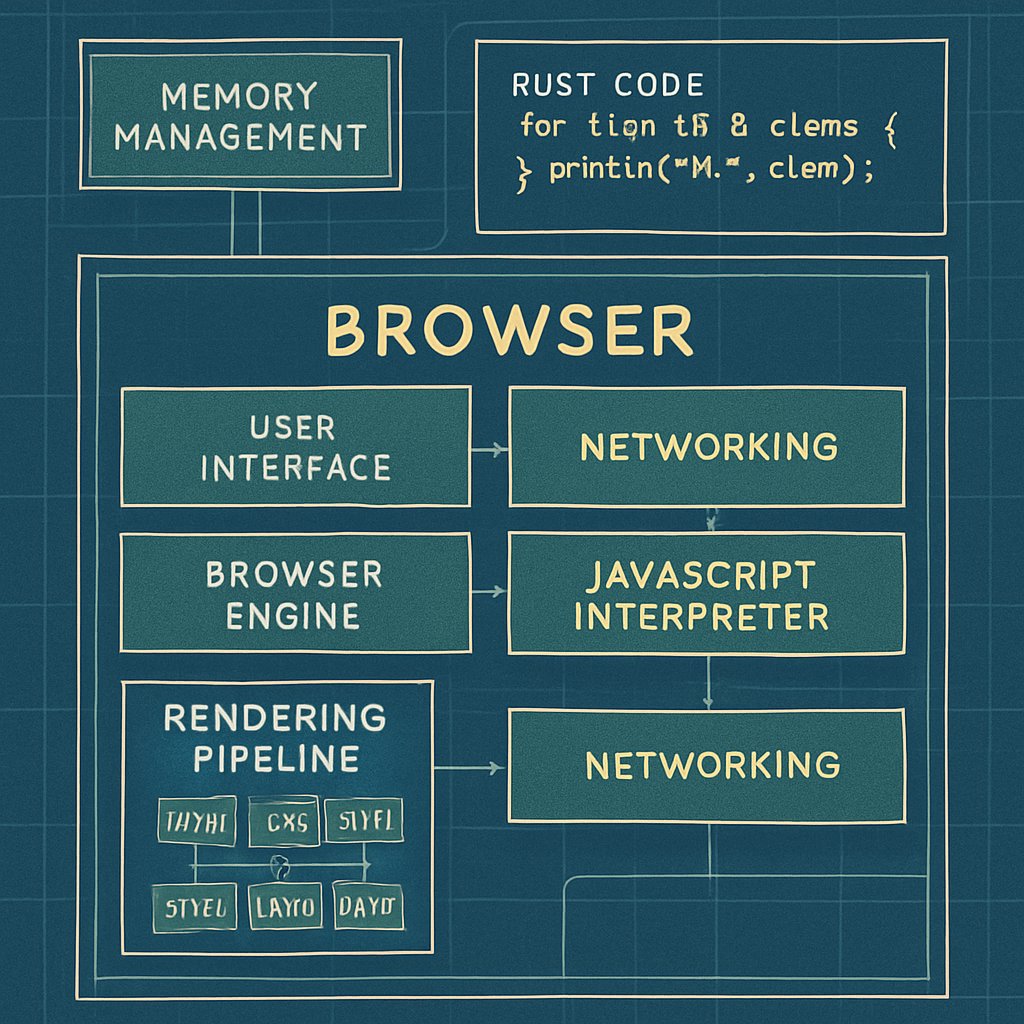
Discover how Ladybird Browser’s adoption of Rust transforms browser security and performance. Learn actionable insights for developers today.
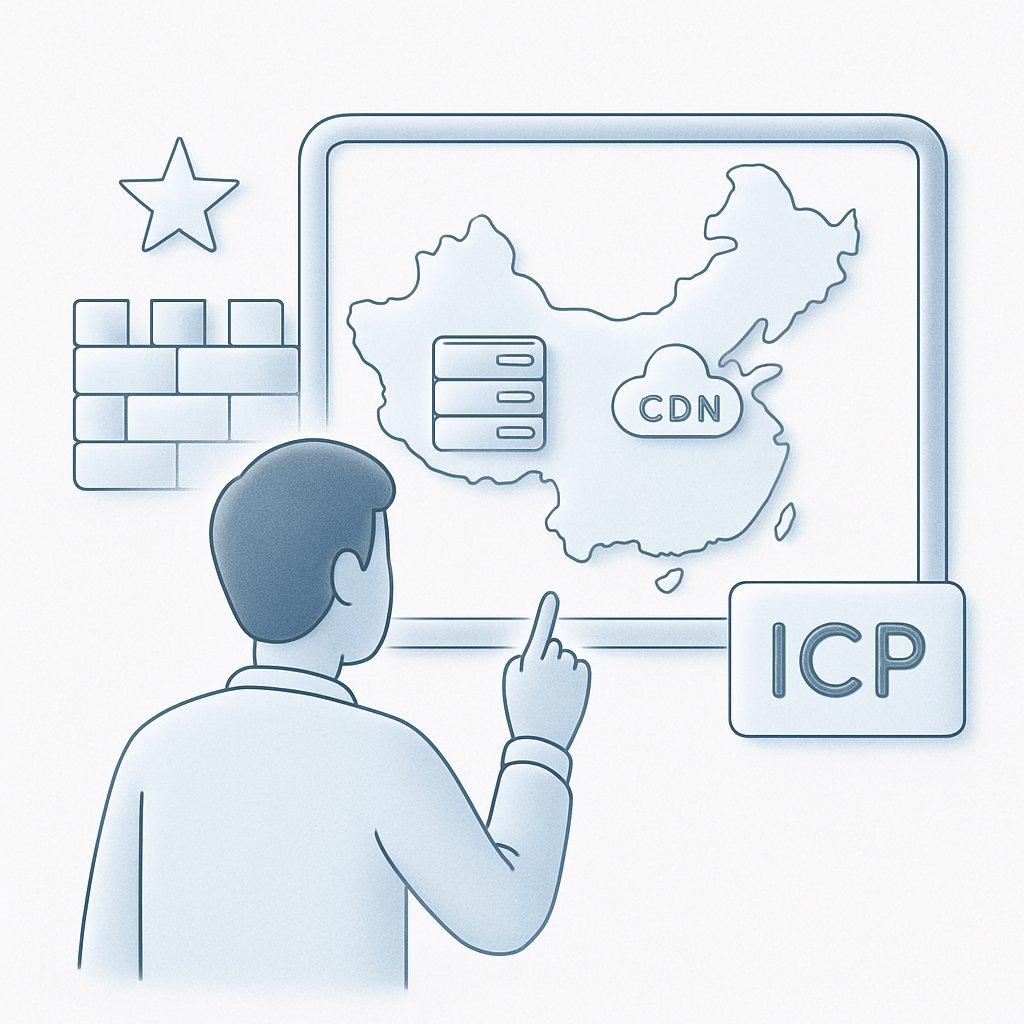
Navigate China’s ICP requirements for website hosting with actionable insights on compliance, hosting options, and performance optimization.

U.S. stocks rallied on February 20, 2026, after the Supreme Court struck down tariffs. Read key market movements, sector performance, and outlook.

Explore phishing-resistant authentication strategies, passkey deployment challenges, and adaptive security measures backed by research.

Discover how the JavaScript Oxidation Compiler (Oxc) boosts performance and streamlines workflows for modern JS/TS development.

Explore how to build a family e-paper dashboard that integrates seamlessly with tech, improving home life without distractions.