Get a quick reference for cloud storage compliance with GDPR, HIPAA, and SOC 2. Use this guide for audits, migrations, and vendor evaluations.
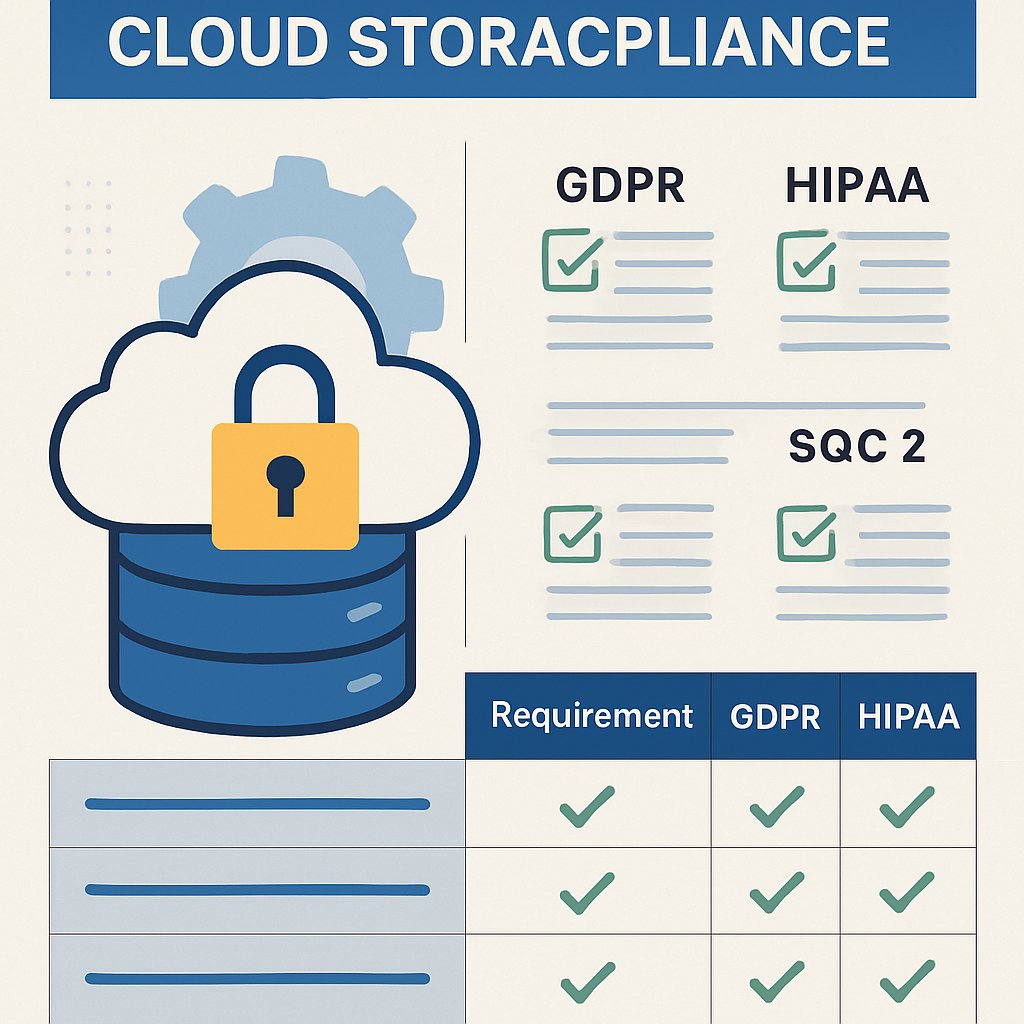

Get a quick reference for cloud storage compliance with GDPR, HIPAA, and SOC 2. Use this guide for audits, migrations, and vendor evaluations.

Explore essential cloud storage compliance for GDPR, HIPAA, and SOC 2. Understand requirements, risks, and best practices for secure data management.