Cloud Encryption: Best practice for Cloud Security
Cloud Encryption is a critical component of Cloud Computing Security Best Practices since it ensures that your cloud data is secured at rest and in transit. It provides peace of mind for customers who store their most sensitive information with the cloud storage companies, as they know those files will be safe from prying eyes? no matter where they go on earth or what device you use to access them Cloud encryption has been around for some time now; its importance only grows as more people turn their computers into mobile workstations via tablets and smartphones. The cloud encryption capabilities of the service provider must be consistent with the sensitivity of the stored data. In this article we will discuss how it works, its importance, challenges, benefits, and how Alibaba Cloud offers high-security infrastructure capabilities, allowing users to store and utilize data securely on a trusted cloud platform.
Cloud encryption’s advantages
In 2021, the threat of data encryption is becoming more and more present. 55% percent of those who have experienced an issue with their company’s cloud services report that unencrypted information poses a problem – which can only be solved by providing them access to encrypted keys or passwords through other means such as two-factor authentication (2FA).
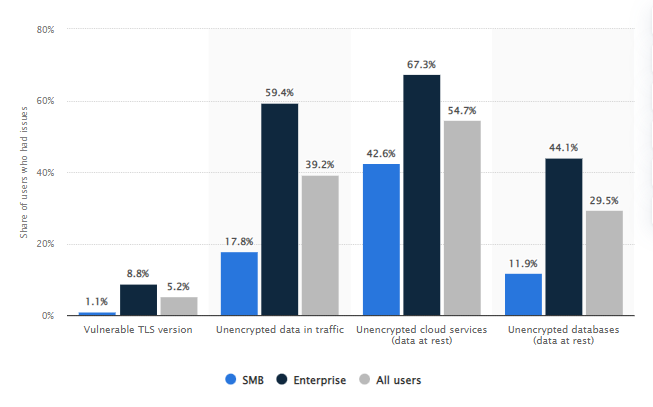
Cloud encryption acts as proactive protection against data breaches and assaults, allowing businesses and their users to use the advantages of cloud collaboration services without jeopardizing data security. It can secure data from end-to-end throughout the transit to and from the cloud and against unwanted access. Additionally, it complies with a large number of consumer and governmental data security standards.
Cloud encryption solutions protect data during transmission to and from cloud-based applications and storage and between users in several locations. Additionally, these technologies encrypt data stored on cloud-based storage devices. These protections prevent unauthorized users from accessing data during its transfer to and from the cloud. Amazon Web Services (AWS), Dropbox, Microsoft Azure, and Google Cloud all provide cloud services that encrypt data at rest.
Difficulties with cloud encryption
While the security benefits of cloud encryption exceed the drawbacks, administrators should be aware of typical issues. Historically, performance and integration issues have prevented many organizations from adopting encryption as a regular practice since the users who need quick access see encryption as excessively complex or inconvenient for users. While modern systems are faster and simpler to use, it is critical to try any platform to verify that integration and usability satisfy needs. Due to the resource-intensive nature of the encryption process, which adds time and money to daily operations, it’s also critical to monitor access times and resource consumption levels.
The loss of encryption keys is a serious issue since it renders all encrypted data unusable, and poor key management may risk essential data. However, the most significant issue is ensuring that any cloud encryption services are in use correctly.
Best Cloud Encryption Approaches
To guarantee compliance issues with the company’s security strategy, security teams should sketch out the security needs for any data that travels to and from the cloud. This will assist in identifying cloud service providers that provide adequate encryption choices and services. Security teams must decide on the following:
- Which data must be encrypted based on its data categorization and compliance requirements
- When encryption is required — in transit, at rest, and during use
- Who should be in possession of the encryption keys — the cloud service provider or the enterprise?
Continous Encryption
All data in transit must encrypt anytime it leaves the internal network. It will always travel through an unknown number of third parties, and it should secure sensitive data even while sent inside. While web browsers and File Transfer Protocol (FTP) software safely handle natively in transit, all connections must utilize a secure protocol. While virtual private networks (VPNs) and IP security (IPsec) are other methods for protecting data in transit, they provide an additional degree of complexity. Cloud access security broker (CASB) solutions provide security administrators with a centralized interface for controlling and managing cloud resources and ensuring users adhere to the organization’s security rules.
Memory and Backup
You should always encrypt and back up critical data locally before transferring it to the cloud. This guarantees that data is accessible and safe in the cloud. Numerous vendors provide robust disc encryption at both the client and network levels. We require Complete disc and memory encryption to protect sensitive data in use, however, this may prevent specific programs from processing the data; thus, tight access controls and limited access to particular data sets are critical alternatives.
Encryption Key
Extensive encryption key management is essential, from key registration to enable complete lifecycle monitoring. The keys should be kept separately from the encrypted data, with off-site backups and frequent auditing. Additionally, administrators should enable multifactor authentication (MFA) for the master and recovery keys. While some cloud encryption companies offer to handle encryption keys, an appealing feature for businesses lacking in-house expertise and resources. However regulatory compliance requirements may compel some to retain and manage keys internally.
Cloud Security in Alibaba Cloud
Alibaba Cloud offers high-security infrastructure capabilities, allowing them to store and utilize data securely on a trusted cloud platform. Alibaba Cloud architecture protects and scans hardware and firmware, and enables a TPM2.0-compliant computing environment. Moreover, it provides hardware encryption (HSM) and chip-level encryption computing capabilities at the cloud platform layer.
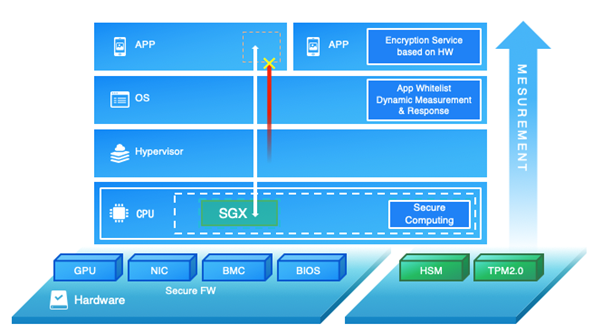
At the cloud product layer, data security integrates with the security aspects of cloud products. It includes end-to-end data encryption, backup, and verification. Among them, end-to-end data encryption is the best data encryption practice.
End-to-end data encryption enables the data encryption on transmission connections, compute nodes, and storage nodes. Specifically, transmission encryption depends heavily on SSL/TLS encryption and protects data using AES256 encryption.
Moreover, it supports AES256 data-at-rest encryption in different products. It also supports Bring Your Own Key (BYOK) through Key Management Service (KMS). Alibaba Cloud, in conjunction with KMS, may offer customers end-to-end data encryption security.
A data encryption process uses globally recognized/standardized encryption methods to generate the ciphertext from plain text data. Proper security protection and management of keys are critical components of the encryption process. If one retains control of the key, one has control of the encryption processes as a whole.
Conclusion
While cloud encryption has a number of disadvantages and difficulties, it is required by standards, laws, and organizational security needs. Security experts would agree that cloud encryption is a critical component of data security. Additionally, cloud service providers provide a variety of encryption solutions to accommodate a variety of budgets and data security requirements.
To enjoy the advantages of cloud encryption, an organization should spend time understanding its data protection requirements and studying the most appropriate and effective encryption services offered by various suppliers in order to avoid putting itself in danger.


