DNS Poisoning Definition:
Domain Name System (DNS) poisoning is a type of cyber-attack that chokes the DNS server to divert the web traffic to non-legitimate destinations. In addition, the user may receive a chain of unwanted unregulated events that can potentially harm the system. Let’s understand DNS poisoning step by step.
Updated On: june 30, 2021
What are DNS and a DNS server?
The DNS is like a telephone directory on the web. We, humans, are much more familiar with domain names rather than confusing IP addresses. But web browsers interact through IP address. So, DNS simply translates those domain names to IP addresses so the browser can retrieve internet resources and the end-user only has to remember the domain name. The process of converting a domain name into an IP address is referred to as DNS resolving.
How does DNS Caching Work?
DNS servers are a collection of servers that involves in the process of DNS resolution. It undergoes multiple steps like root name server, top-level domain name server, authority name server lookups. Giant service providers do the complete networking setup and provide DNS as a service to the end-user. Cloudflare, Google DNS, Quad9, ClouDNS, Akamai DNS are some of the most popular DNS providers.
DNS resolver basically helps in converting IP addresses to domain names. A DNS resolver will store the request queries for a certain amount of time (TTL –Time to Live). This is how the resolver will be able to serve the request more quickly without communicating further with other DNS networks.
Now let’s talk about DNS Poisoning:
Imagine a huge bunch of keys tagged with their associated correct locks?. Now the culprit rushes and shuffles the key tags intentionally and leaves the room. The manager will put a hell of a lot of effort but won’t get lucky in finding the key for a particular lock just because the tags are mismatched. Let’s relate this with DNS poisoning.
Domain Name Server (DNS) cache poisoning is an attack in which altered DNS records are used to redirect online traffic to a malicious website that resembles its intended destination. Here, locks are the IP addresses and tags are the DNS records. We won’t be able to open the lock until we attach the correct key. Same as this, traffic will be redirected to the wrong place until DNS records are inaccurate.
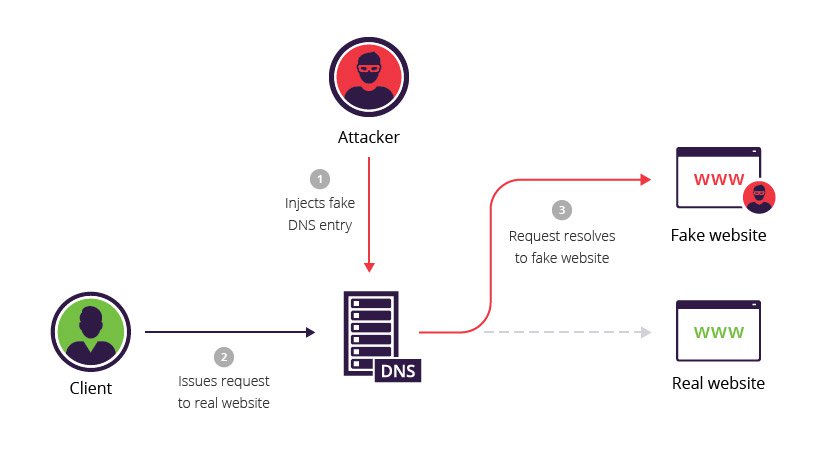
How is DNS poisoning done?
A DNS can become poisoned if it contains incorrect entries. Attackers poison the DNS records by impersonating the nameservers and alters the reply for that query. Hence, the user will get totally unexpected results. And if the DNS resolver fetches the wrong entry, there is no legitimate source to verify that value.
For example, if an unauthorized party gets control of a DNS server and changes some entries in it like pointing the domain X to some other IP address. So any user request for the domain X will be redirected to the incorrect IP (usually this IP belongs to attackers) and that website may breach the user privacy or data.
And as the theory says “poison”, it spreads.! Yes, with various poisoned DNS records, it may spread across the internet and incorrect entries will be cached.
DNS Poisoning Process:
Mostly, DNS services work on UDP protocol which is extremely fast but volatile at the same time. UDP protocol does not require any acknowledgment of the communication and there lies the whole trap. Whereas, TCP requires both ways of communication to initiate and verify the connection. With UDP, there is no such guarantee that a connection is open and the receiver is active and verify who the sender is. The attackers actually use this and perform the exploitation on DNS and pretend that the response is coming from a legit source.
This looks vulnerable but not as easy as it looks. The attacker has very little time to peak in and pass their entries as the DNS resolver also queries the authority name server.
The Great Firewall of China:
The Great Firewall of China is an example of DNS poisoning on a very large scale. One of the primary methods of query filtering that the GFW relies on is DNS response poisoning. When a query is poisoned by the GFW, the infected or altered result is returned. This leads to the inaccessibility of the websites which come under GFW compliance. Twitter, Facebook are some of the examples.
Solution:
DNS level security is the solution. We can implement some setup where we can verify the entries and their integrity. Adding a layer of cryptography is a plus. This will ensure that the records are original and not exploited in between. DNSSEC (Domain Name System Security Extensions) is a collection of extensions for securing data communication in DNS.
Using VPN is also a considerable workaround as it allows communication via encrypted tunnels and adds an extra level of security. Checkout VPN basics in this article.

